September 09, 2022
When a DDoS attack comes, defend your applications with an AWS firewall
CDW Managed Services for AWS protects customer web applications using AWS WAF Security Automations.

Amazon Web Services Web Application Firewall (AWS WAF) is an AWS Cloud service that helps protect a web application or application programming interface (API) from common assaults, such as structured query language (SQL) injections, distributed denial of service (DDoS) attacks, cross-site scripting, etc. It can be deployed as a firewall in front of an AWS Application Load Balancer (ALB), Amazon CloudFront, Amazon API Gateway or AWS AppSync.
CDW Managed Services for AWS uses AWS WAF as the go-to solution for our customers looking for a robust and AWS native security solution with fine-grained control over requests attempting to access web applications running in Amazon Web Services.
AWS WAF sits in line and in parallel with an ALB. The ALB receives and decrypts transport layer security (TLS) connections and sends the request to the WAF service for evaluation. Using its configured firewall rules, the WAF marks the request as ACCEPT/REJECT for further processing.
AWS WAF and ALB Reference Architecture
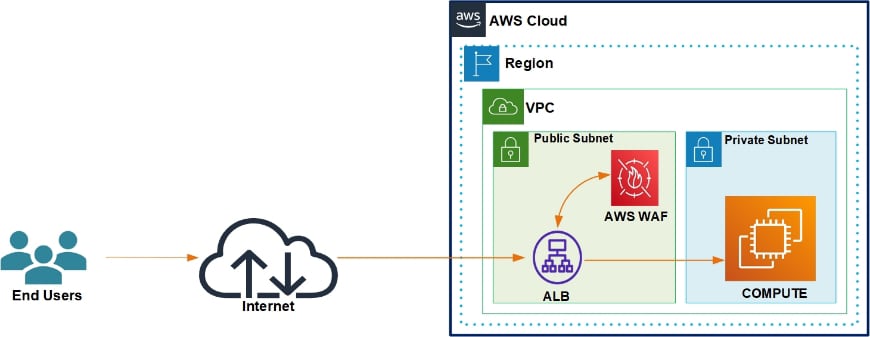
A recent example of how CDW Managed Services for AWS utilized AWS WAF is for a university in California. The university’s publicly accessible website, which is 100 percent hosted in AWS, experienced a DDoS attack.
During the attack, the website became completely inaccessible due to a surge in the number of requests that was being sent. Within a very short period, the website’s request count increased from 4,000 to more than 20,000, exceeding the Classic Load Balancer SurgeQueueLength maximum of 1,024 counts per second. The attack overwhelmed the customer’s backend web and database infrastructure with memory and CPU spikes of up to 99 percent regardless of the number Elastic Cloud Compute (EC2) instances initiated by auto scaling.
The customer needed an immediate solution to stop the attack as well as preventive measures to mitigate any future attacks. The customer web application was running on the deprecated Classic Load Balancer, which does not support AWS WAF v2. CDW Engineers immediately created a new AWS Elastic Beanstalk environment using existing AWS CodePipeline, upgraded/migrated the Classic Load Balancers to an Application Load Balancer and deployed AWS WAF Security Automations.
After the implementation, CDW engineers configured multiple rules on the WAF to address SQL Injection, HTTP flood, scanners and probes and bad bots attacks. An IP reputation list was also put in place to check and block blacklisted IP addresses, as was a manual IP list, which gave the customer additional options to block/allow IPs as deemed necessary.
Since its implementation, the customer’s website has been up and running and the AWS WAF solution has been effective at stopping and preventing unwanted or bad actors.
AWS WAF Security Automations Reference Architecture
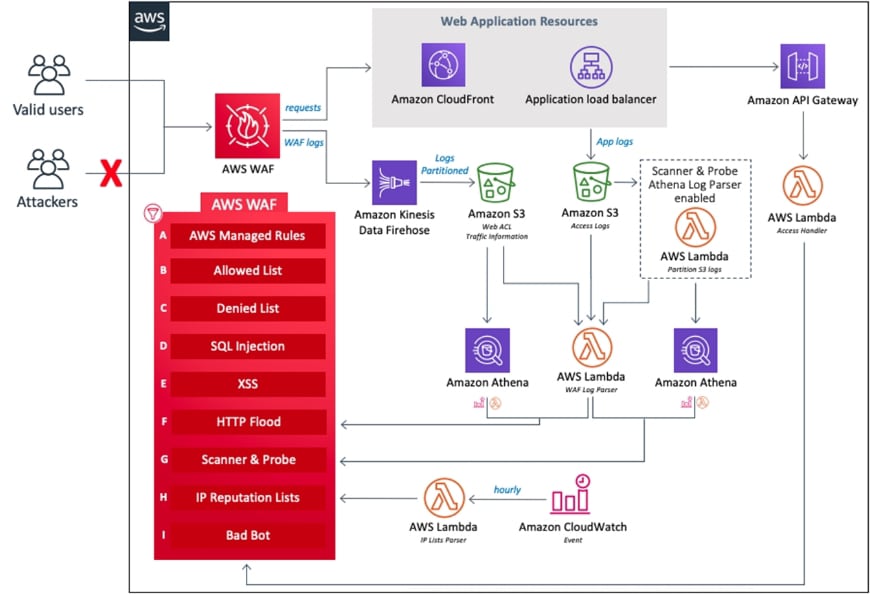
Diagram Source: AWS Security WAF Automations
Story by Isaac Oben, a Cloud Security Manager at CDW Integrated Tech where he assists cloud customers in solving technology and security challenges. He is an active member of the AWS Partner Network where he is recognized as an AWS Ambassador and holds an AWS Security Black Belt designation.

